Introduction
This example is improved (different) version of round-robin load balancing example. It adds persistent user sessions, i.e. a particular user would use the same source IP address for all outgoing connections. Consider the following network layout: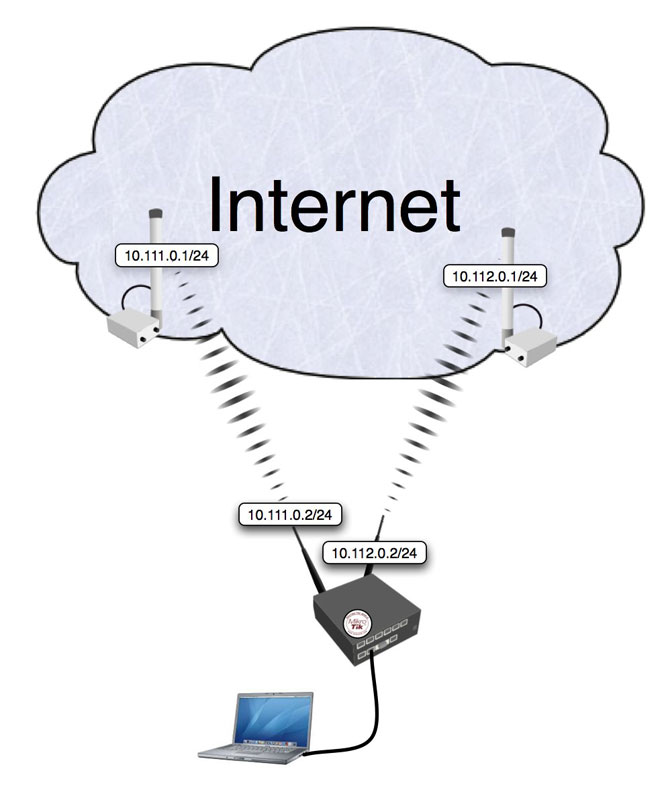
Quick Start for Impatient
Configuration export from the gateway router:/ ip address
add address=192.168.0.1/24 network=192.168.0.0 broadcast=192.168.0.255 interface=Local
add address=10.111.0.2/24 network=10.111.0.0 broadcast=10.111.0.255 interface=wlan2
add address=10.112.0.2/24 network=10.112.0.0 broadcast=10.112.0.255 interface=wlan1
/ ip firewall mangle
add chain=prerouting src-address-list=odd in-interface=Local action=mark-connection \
new-connection-mark=odd passthrough=yes
add chain=prerouting src-address-list=odd in-interface=Local action=mark-routing \
new-routing-mark=odd passthrough=no
add chain=prerouting src-address-list=even in-interface=Local action=mark-connection \
new-connection-mark=even passthrough=yes
add chain=prerouting src-address-list=even in-interface=Local action=mark-routing \
new-routing-mark=even passthrough=no
add chain=prerouting in-interface=Local connection-state=new nth=2,1 \
action=mark-connection new-connection-mark=odd passthrough=yes
add chain=prerouting in-interface=Local action=add-src-to-address-list \
address-list=odd address-list-timeout=1d connection-mark=odd passthrough=yes
add chain=prerouting in-interface=Local connection-mark=odd action=mark-routing \
new-routing-mark=odd passthrough=no
add chain=prerouting in-interface=Local connection-state=new nth=2,2 \
action=mark-connection new-connection-mark=even passthrough=yes
add chain=prerouting in-interface=Local action=add-src-to-address-list \
address-list=even address-list-timeout=1d connection-mark=even passthrough=yes
add chain=prerouting in-interface=Local connection-mark=even action=mark-routing \
new-routing-mark=even passthrough=no
/ ip firewall nat
add chain=srcnat out-interface=wlan1 action=masquerade
add chain=srcnat out-interface=wlan2 action=masquerade
/ ip route
add dst-address=0.0.0.0/0 gateway=10.111.0.1 scope=255 target-scope=10 routing-mark=odd
add dst-address=0.0.0.0/0 gateway=10.112.0.1 scope=255 target-scope=10 routing-mark=even
add dst-address=0.0.0.0/0 gateway=10.112.0.1 scope=255 target-scope=10
Explanation
First we give a code snippet and then explain what it actually does.IP Addresses
/ ip address add address=192.168.0.1/24 network=192.168.0.0 broadcast=192.168.0.255 interface=Local add address=10.111.0.2/24 network=10.111.0.0 broadcast=10.111.0.255 interface=wlan2 add address=10.112.0.2/24 network=10.112.0.0 broadcast=10.112.0.255 interface=wlan1The router has two upstream (WAN) interfaces with the addresses of 10.111.0.2/24 and 10.112.0.2/24. The LAN interface has the name "Local" and IP address of 192.168.0.1/24.
Mangle
/ ip firewall mangle add chain=prerouting src-address-list=odd in-interface=Local action=mark-connection \ new-connection-mark=odd passthrough=yes add chain=prerouting src-address-list=odd in-interface=Local action=mark-routing \ new-routing-mark=odd
All traffic from customers having their IP address previously placed in the address list "odd" is instantly marked with connection and routing marks "odd". Afterwards the traffic is excluded from processing against successive mangle rules in prerouting chain.
/ ip firewall mangle add chain=prerouting src-address-list=even in-interface=Local action=mark-connection \ new-connection-mark=even passthrough=yes add chain=prerouting src-address-list=even in-interface=Local action=mark-routing \ new-routing-mark=even
Same stuff as above, only for customers having their IP address previously placed in the address list "even".
/ ip firewall mangle
add chain=prerouting in-interface=Local connection-state=new nth=2,1 \
action=mark-connection new-connection-mark=odd passthrough=yes
add chain=prerouting in-interface=Local action=add-src-to-address-list \
address-list=odd address-list-timeout=1d connection-mark=odd passthrough=yes
add chain=prerouting in-interface=Local connection-mark=odd action=mark-routing \
new-routing-mark=odd passthrough=no
First we take every second packet that establishes new session (note connection-state=new), and mark it with connection mark "odd". Consequently all successive packets belonging to the same session will carry the connection mark "odd". Note that we are passing these packets to the second and third rules (passthrough=yes). Second rule adds IP address of the client to the address list to enable all successive sessions to go through the same gateway. Third rule places the routing mark "odd" on all packets that belong to the "odd" connection and stops processing all other mangle rules for these packets in prerouting chain.
/ ip firewall mangle
add chain=prerouting in-interface=Local connection-state=new nth=2,2 \
action=mark-connection new-connection-mark=even passthrough=yes
add chain=prerouting in-interface=Local action=add-src-to-address-list \
address-list=even address-list-timeout=1d connection-mark=even passthrough=yes
add chain=prerouting in-interface=Local connection-mark=even action=mark-routing \
new-routing-mark=even passthrough=no
These rules do the same for the remaining half of the traffic as the first three rules for the first half of the traffic.
The code above effectively means that each new connection initiated through the router from the local network will be marked as either "odd" or "even" with both routing and connection marks.
The above works fine. There are however some situations where you might find that the same IP address is listed under both the ODD and EVEN scr-address-lists. This behavior causes issues with apps that require persistent connections. A simple remedy for this situation is to add the following statement to your mangle rules:
add chain=prerouting in-interface=Local connection-state=new nth=2,2 \
src-address-list=!odd action=mark-connection new-connection-mark=even \
passthrough=yes
This will ensure that the new connection will not already be part of
the ODD src-address-list. You will have to do the same for the ODD
mangle rule thus excluding IP's already part of the EVEN
scr-address-list.
NAT
/ ip firewall nat add chain=srcnat out-interface=wlan1 action=masquerade add chain=srcnat out-interface=wlan2 action=masqueradeFix the source address according to the outgoing interface.
Routing
/ ip route add dst-address=0.0.0.0/0 gateway=10.111.0.1 scope=255 target-scope=10 routing-mark=odd add dst-address=0.0.0.0/0 gateway=10.112.0.1 scope=255 target-scope=10 routing-mark=evenFor all traffic marked "odd" (consequently having 10.111.0.2 translated source address) we use 10.111.0.1
gateway. In the same manner all traffic marked "even" is routed through the 10.112.0.1 gateway.
/ ip route add dst-address=0.0.0.0/0 gateway=10.112.0.1 scope=255 target-scope=10
Finally, we have one additional entry specifying that traffic from the router itself (the traffic without any routing marks) should go to 10.112.0.1 gateway.
note:
http://wiki.mikrotik.com/wiki/NTH_load_balancing_with_masquerade




